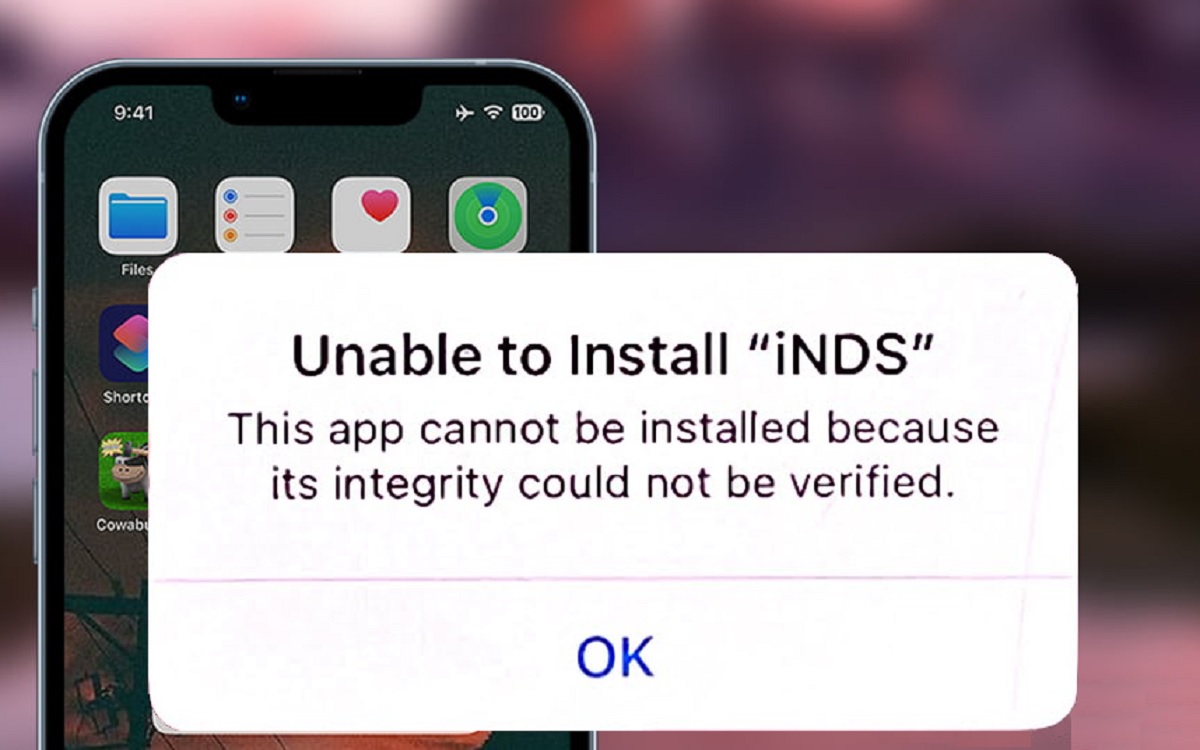
In today’s digital landscape, our smartphones have become an integral part of our lives, storing sensitive information and serving as gateways to countless online services. As we rely more heavily on these devices, ensuring the security and integrity of the applications we install becomes paramount. With the upcoming release of iOS 17, Apple is introducing a powerful feature called “Verify App Integrity,” designed to safeguard your iPhone against potential threats and maintain the integrity of your app ecosystem.
Recent Released:How to Clear App Cache iOS On Apple Vision Pro
How to Understand App Integrity
App integrity refers to the state of an application being unmodified, unaltered, and free from tampering or corruption. When an app’s integrity is compromised, it can potentially expose users to various risks, including data breaches, malware infections. Unauthorized access to sensitive information. Maintaining app integrity is crucial for ensuring the security and privacy of your device and personal data.
The Need for Verification
In the ever-evolving world of cybersecurity, threats are constantly emerging, and malicious actors are consistently finding new ways to exploit vulnerabilities. One common method of attack is the distribution of modified or tampered versions of legitimate apps. Often disguised as updates or third-party installations. These malicious apps can contain hidden malware, backdoors, or other malicious code designed to steal data. Gain unauthorized access, or disrupt the normal functioning of your device.
By verifying the integrity of installed apps, iOS 17 aims to detect and prevent the installation and execution of compromised or untrusted applications, effectively mitigating these risks and protecting your device from potential harm.
How “Verify App Integrity” Works
The “Verify App Integrity” feature in iOS 17 leverages advanced cryptographic techniques to ensure that the apps installed on your device are genuine and have not been modified or tampered with. Here’s how it works:
Here’s how it works
- App Signing and Verification: Apple requires all apps distributed through the App Store to be digitally signed with a valid certificate issued by Apple. This digital signature acts as a seal of authenticity. Ensuring that the app originates from a trusted source and has not been altered since its release. When an app is installed on your iPhone, iOS 17 automatically verifies the digital signature to confirm its integrity. If the signature is invalid or has been tampered with, the installation process will be halted, and the user will be alerted about the potential security risk.
- Code Integrity Checks:
- Code Integrity Checks: In addition to verifying the digital signature, iOS 17 performs comprehensive code integrity checks on installed apps. This process involves analyzing the app’s executable code, libraries, and resources to detect any unauthorized modifications or deviations from the original, trusted version. By comparing the app’s code against a known, secure reference, iOS 17 can identify any anomalies or discrepancies that may indicate tampering or the presence of malicious code. If any suspicious changes are detected, the app will be flagged as untrusted, and its execution will be prevented.
- Continuous Monitoring: The “Verify App Integrity” feature doesn’t stop at the installation stage.
- iOS 17 continuously monitors installed apps for any changes or modifications that may occur during their lifetime. This ongoing monitoring ensures that even if an app is initially trusted, any subsequent tampering or corruption will be detected and addressed promptly. If an app is found to have been modified after installation, iOS 17 will take appropriate action. Such as revoking the app’s permissions, disabling its functionality, or prompting the user to reinstall the legitimate version from the App Store.
What is Benefits of Verifying App Integrity
By implementing the “Verify App Integrity” feature, iOS 17 offers several key benefits to users, developers. The overall security ecosystem:
- Enhanced Security and Privacy: Verifying app integrity helps protect your device from potential threats posed by malicious or compromised apps. By ensuring that only trusted and unmodified apps can run on your iPhone.
- iOS 17 significantly reduces the risk of data breaches, malware infections, and unauthorized access to sensitive information.
- Maintaining App Functionality: App developers invest significant time and effort into creating and maintaining their apps. By verifying app integrity, iOS 17 helps ensure that apps function as intended. Without any unintended modifications or alterations that could disrupt their performance or introduce unexpected behaviors.
- Fostering Trust in the App Ecosystem: The App Store is a curated platform. Apple takes great care to review and approve apps before making them available for download. By implementing robust integrity checks, iOS 17 reinforces the trust users have in the App Store and the overall app ecosystem. Giving them confidence that the apps they install are safe and reliable.
- Encouraging Responsible App Development: With the “Verify App Integrity” feature in place. Developers have an added incentive to follow best practices and adhere to Apple’s guidelines for app development and distribution. This not only promotes a more secure app ecosystem but also encourages innovation and the creation of high-quality apps that prioritize user safety and privacy.
Embracing the “Verify App Integrity” Feature
As we eagerly await the release of iOS 17, it is essential to understand the importance of the “Verify App Integrity” feature and its role in safeguarding your iPhone and personal data. By leveraging advanced security mechanisms and continuous monitoring. This feature ensures that the apps you install and use are genuine, unmodified, and free from potential threats.
To fully benefit from this feature, it is recommended to keep your iPhone updated with the latest iOS version. To only install apps from trusted sources, such as the App Store. Additionally, be cautious of unsolicited app updates or prompts to install apps from unknown sources. As these could be attempts to bypass the integrity checks and introduce malicious code.
In the ever-evolving digital landscape, security and privacy should be top priorities. By embracing the “Verify App Integrity” feature in iOS 17, you can enjoy a safer and more secure app experience. While protecting your personal information and maintaining the integrity of your device.
Conclusion
The “Verify App Integrity” feature in iOS 17 represents a significant step forward in Apple’s commitment to user security and privacy. By implementing robust app integrity checks and continuous monitoring. This feature helps ensure that the apps running on your iPhone are genuine, unmodified, and free from potential threats.
As technology continues to advance and cyber threats evolve. It is crucial to stay vigilant and take advantage of the security measures offered by modern operating systems like iOS 17. By verifying app integrity, you can enjoy a safer and more secure app ecosystem. While maintaining trust in the apps you use and the platforms that distribute them.
Remember, security is an ongoing process, and it is essential to keep your device updated. Be cautious of unsolicited app installations, and only download apps from trusted sources. By embracing the “Verify App Integrity” feature and following best practices. You can protect your iPhone, safeguard your personal data, and contribute to a more secure and trustworthy digital world.
Useful Table: Common App Integrity Issues and Mitigation Strategies
| Issue | Description | Mitigation Strategy |
| Tampered or Modified Apps | Apps that have been altered or modified by unauthorized parties, potentially introducing malicious code or functionality. | Use the “Verify App Integrity” feature to detect and prevent the installation and execution of tampered apps. Only install apps from trusted sources like the App Store. |
| Outdated or Vulnerable Apps | Apps that contain known vulnerabilities or security flaws due to lack of updates or proper maintenance. | Keep apps up-to-date by installing the latest available updates from the App Store. Uninstall and replace apps that are no longer supported or maintained by the developer. |
| Untrusted or Unofficial App Stores | App stores or repositories that are not officially sanctioned by Apple, potentially distributing malicious or compromised apps. | Only install apps from the official App Store, which is curated and maintained by Apple. Avoid installing apps from untrusted or unofficial sources. |
| Jailbroken or Rooted Devices | Devices that have been jailbroken or rooted, bypassing built-in security mechanisms and potentially exposing them to threats. | Avoid jailbreaking or rooting your device, as it can compromise the integrity of the operating system and make it more vulnerable to attacks. |
| Phishing and Social Engineering Attacks | Attempts to trick users into installing malicious apps by disguising them as legitimate or trusted apps. | Be cautious of unsolicited app installation prompts or links, and always verify the authenticity of apps before installing them. Implement security awareness training for users. |
| Physical Device Tampering | Unauthorized physical access to a device, which could potentially lead to the installation of malicious apps or hardware-based attacks. | Implement physical security measures, such as device encryption, strong access controls, and monitoring for unauthorized access attempts. |
By understanding and addressing these common app integrity