Introduction
Apple has taken a proactive stance to protect its users from the latest wave of Phishing scams. With the emergence of a new SMS threat, the tech giant has released a comprehensive set of guidelines to help users safeguard their personal information and maintain the integrity of their Apple IDs. This article Examine into these crucial tips, providing you with the knowledge and tools to stay one step ahead of cybercriminals.
Recent Released: How To Download And Play Grindstone iPhone Games
The Golden Rule: Never Share Sensitive Information
The Importance of Keep Personal Data Private
In the digital age, personal data is akin to currency. Cybercriminals are constantly devising new ways to trick users into divulging sensitive information. Apple emphasizes that under no circumstances should users share personal data, especially passwords and security codes. This information is the key to your digital kingdom, and sharing it is akin to handing over the keys to your house to a stranger.
Recognize Attempts to Extract Security
Information Scammers often disguise their attempts to extract information as legitimate requests. They may create webpages that look strikingly similar to official Apple login pages. However, Apple stresses that they will never direct you to enter your security information on a webpage through an unsolicited message. Always access your Apple account directly through the official app or website.
Fortify Your Apple ID
Implement Two-Factor Authentication
Two-factor authentication (2FA) is a powerful tool in your cybersecurity arsenal. By requiring a second form of verification beyond your password, 2FA significantly reduces the risk of unauthorized access to your account, even if your password is compromised.
Maintain Secure and Updated Contact Information
Keeping your contact information up-to-date is crucial for account recovery and security notifications. Regularly review and update your email addresses and phone numbers associated with your Apple ID to ensure you can always regain access to your account and receive important security alerts.
The Sacred Nature of Your Apple ID Password
Your Apple ID password is the master key to your entire Apple ecosystem. Apple emphasizes that they will never ask for your password or verification codes to provide support. Treat these credentials as you would your most valuable possessions – never share them with anyone, regardless of how legitimate they may seem.
The Gift Card Trap: A Common Scam Tactic
How toUnderstand Why Scammers Request Gift Card Payments
Gift cards are a favorite tool of scammers because they’re difficult to trace and essentially function as digital cash. Apple warns that they should never be used to make payments to other individuals. If someone is pressuring you to make a payment using Apple Gift Cards, it’s almost certainly a scam.
Legitimate Uses of Apple Gift Cards
Apple Gift Cards are designed for purchasing apps, games, music, movies, TV shows, iCloud storage, and other Apple services. They are not intended for person-to-person transactions or to pay for non-Apple services. Understanding their proper use can help you quickly identify when a request is illegitimate.
Navigate the Sea of Emails: Identify Authentic Apple Communications
Basic Features of Genuine Apple Emails
Apple provides detailed information on how to identify legitimate emails about App Store or iTunes Store purchases. These emails typically include specific transaction details and do not ask for sensitive information. Familiarizing yourself with the characteristics of genuine Apple emails can help you spot fakes more easily.
Red Flags in Suspicious Messages
Suspicious emails often contain generic greetings, urgent language, and requests for immediate action. They may also have spelling or grammatical errors. Be particularly wary of emails that ask you to click on links or download attachments, especially if they create a sense of urgency.
The Link and Attachment Minefield
The Dangers Lurking in Suspicious Links
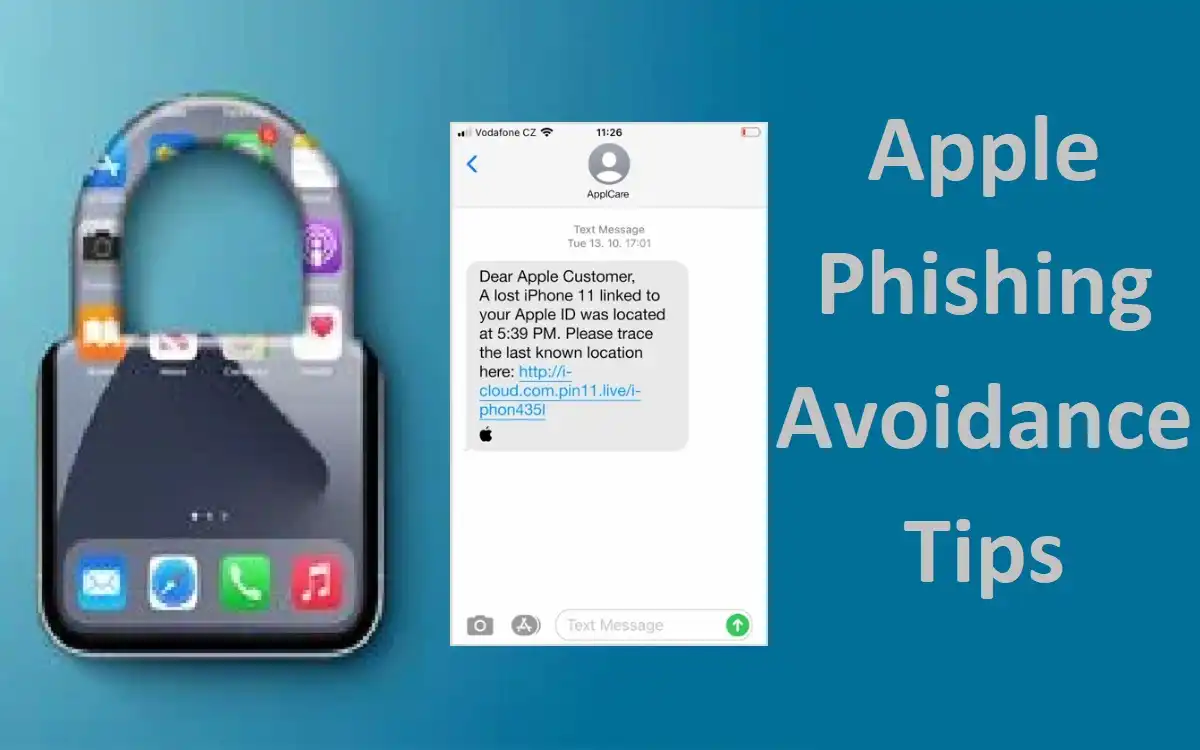
Phishing attempts often rely on deceptive links that lead to fake websites designed to steal your information. Apple advises never to follow links in suspicious or unsolicited messages. Instead, always navigate directly to Apple’s official website or use the official Apple app to check your account status or make changes.
Why You Should Never Open Unsolicited Attachments
Attachments in phishing emails can contain malware that can infect your device and compromise your security. Apple recommends never opening or saving attachments from unknown or suspicious sources, regardless of how enticing they may seem.
Recognize and Respond to Suspicious Contact Attempts
Handle Dubious Phone Calls
Scammers may impersonate Apple support representatives over the phone. Apple emphasizes that they will never call you unsolicited to ask for sensitive information. If you receive a suspicious call claiming to be from Apple, hang up and contact Apple support directly through their official channels.
Deal with Questionable Messages
Similar to phone calls, be wary of unsolicited text messages or instant messages claiming to be from Apple. These often contain links to phishing websites. Ignore and delete such messages without engaging with them.
Proper Channels for Contact
Apple Support If you have concerns about your Apple account or services, always initiate contact through official Apple support channels. This ensures you’re communicating with genuine Apple representatives and not falling victim to a scam.
Unmask Urgency: The Scammer’s Favorite Tool
Common Scare Tactics
Used by Cybercriminals Scammers often create a false sense of urgency to pressure victims into hasty actions. They may claim your personal information has been stolen or that unauthorized charges have been made to your account. Remember, legitimate companies like Apple don’t use such tactics.
The Truth About How Apple Handles Security Issues
Apple has established protocols for dealing with security concerns, which never involve pressuring users or requesting immediate action through unsecured channels. Understanding Apple’s actual practices can help you identify when a request is not legitimate.
Steer Clear of Malicious Software and Profiles
The Risks of Unrecognized Software
Downloading software from unverified sources can introduce malware to your device. Apple advises only downloading apps from the official App Store and being cautious of any pop-up messages asking you to take action or download software.
Understand Configuration
Profiles and Their Potential Dangers Configuration profiles can give extensive control over your device to third parties. Apple recommends only installing profiles from trusted sources, such as your employer or educational institution, and being extremely cautious of any unexpected profile installation requests.
Take Action: Report Suspicious Activity
How to Report Phishing Attempts to Apple
Apple encourages users to report suspicious emails by forwarding them to reportphishing@apple.com. This helps Apple improve their security measures and protect other users from similar threats.
9.2 The Importance of Screenshots in Report
FaceTime Fraud For suspicious FaceTime calls or links, Apple recommends taking screenshots and sending them to. These reports are crucial in helping Apple identify and combat new scam tactics.
Stay Informed: Keeping Up with the Latest Threats
Resources for Learn About
New Scams Staying informed about the latest phishing tactics is crucial in maintaining your digital security. Apple regularly updates its support pages with information about new threats and how to avoid them.
Apple’s Ongo Efforts to Combat Phish
Apple is continuously working to improve its security measures and educate users about potential threats. By staying engaged with Apple’s security updates and following their guidelines, you can significantly reduce your risk of falling victim to phishing scams.
Conclusion
As digital SMS Threat continue to evolve, staying vigilant and informed is crucial to protecting your personal information and digital identity. By following Apple’s comprehensive guidelines, you can significantly reduce your risk of falling victim to phishing scams and other cybersecurity threats. Remember, your best defense is a combination of skepticism, caution, and adherence to best practices in digital security. Stay safe, stay informed, and always think twice before sharing sensitive information online.
Table: Quick Reference Guide for Identify and Respond to Phishing Attempts
| Scenario | Red Flags | Appropriate Action |
| Unexpected email requesting personal information | Urgent tone, generic greetings, suspicious sender address | Do not respond or click links; forward to reportphishing@apple.com |
| SMS with link to “verify” Apple ID | Unsolicited message, pressure to act quickly | Do not click the link; delete the message |
| Phone call claiming to be Apple support | Caller requests sensitive information, uses scare tactics | Hang up and contact Apple support through official channels |
| Pop-up asking to download software | Unexpected request, unfamiliar software name | Close the pop-up without interacting; check for system updates through official means |
| Request to make payment with Apple Gift Cards | Any scenario outside of App Store or iTunes purchases | Refuse the request; report to Apple and local authorities if necessary |
| Email about unauthorized App Store purchase | Sender address not from @apple.com, poor grammar/spelling | Do not click links; check purchase history directly in App Store |